LDAP
Lightweight Directory Access Protocol (LDAP) is an access protocol used to access and manage directory information, providing the ability to authenticate organizational users across many applications.
In Corellium, LDAP can be used to allow users to log in with their LDAP credentials and assign users to Corellium teams based on their LDAP groups.
Enable LDAP for Your Domain
To enable LDAP from an existing Corellium domain, follow the steps below:
-
Log in as the domain administrator and navigate to the Admin -> Authentication page.
-
Click on the "Enable LDAP authentication" toggle.
-
Set your Server Connection Details tab, fill in your LDAP server URL and optional port, and click Update changes.
- Optionally enable LDAPS to secure the connection to the LDAP server.
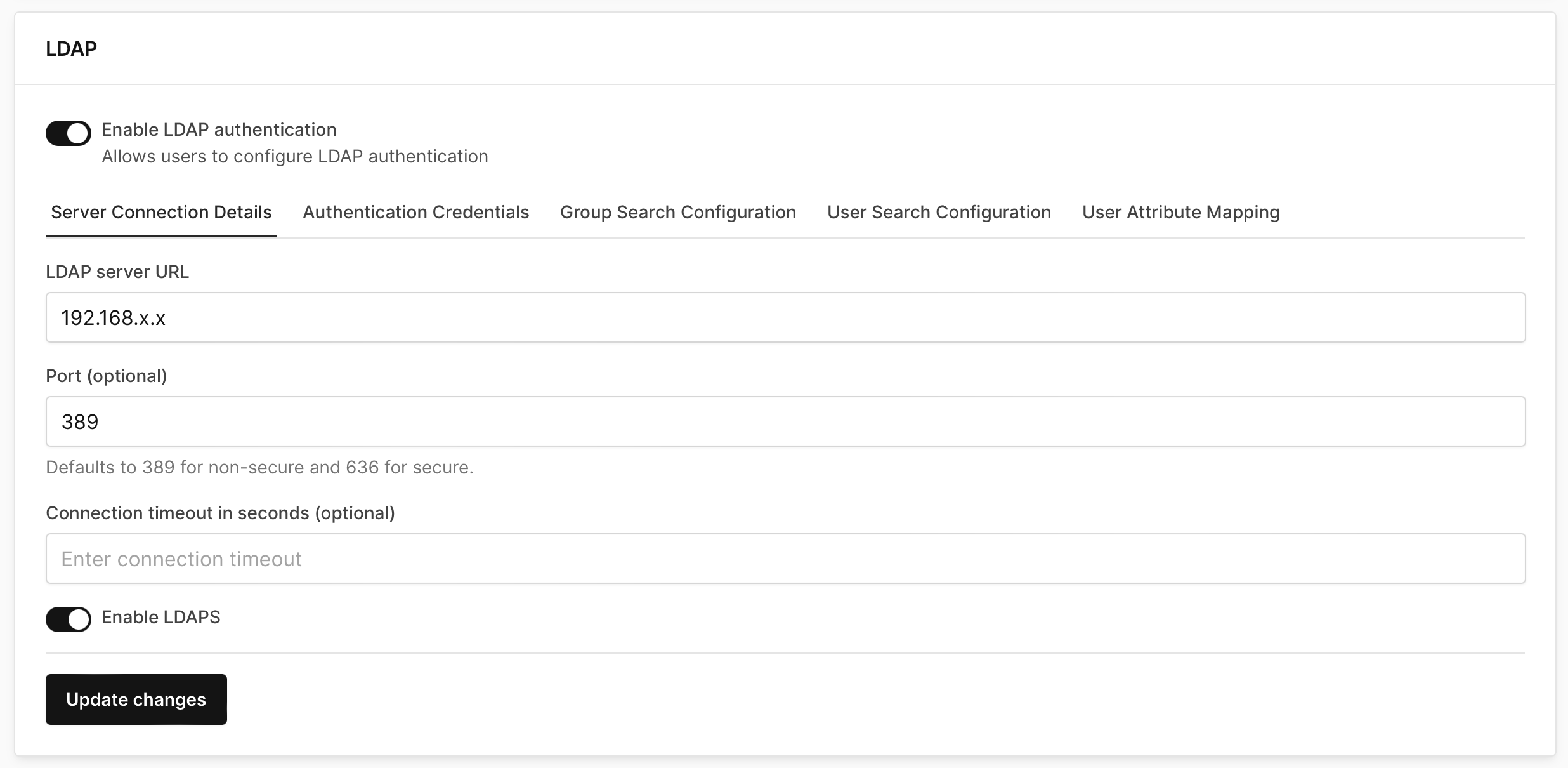
-
In the Authentication Credentials tab, set your Bind Distinguished Name and Bind Password for the LDAP administrator account.
- An example of a Bind DN is
cn=admin,dc=corellium,dc=co.
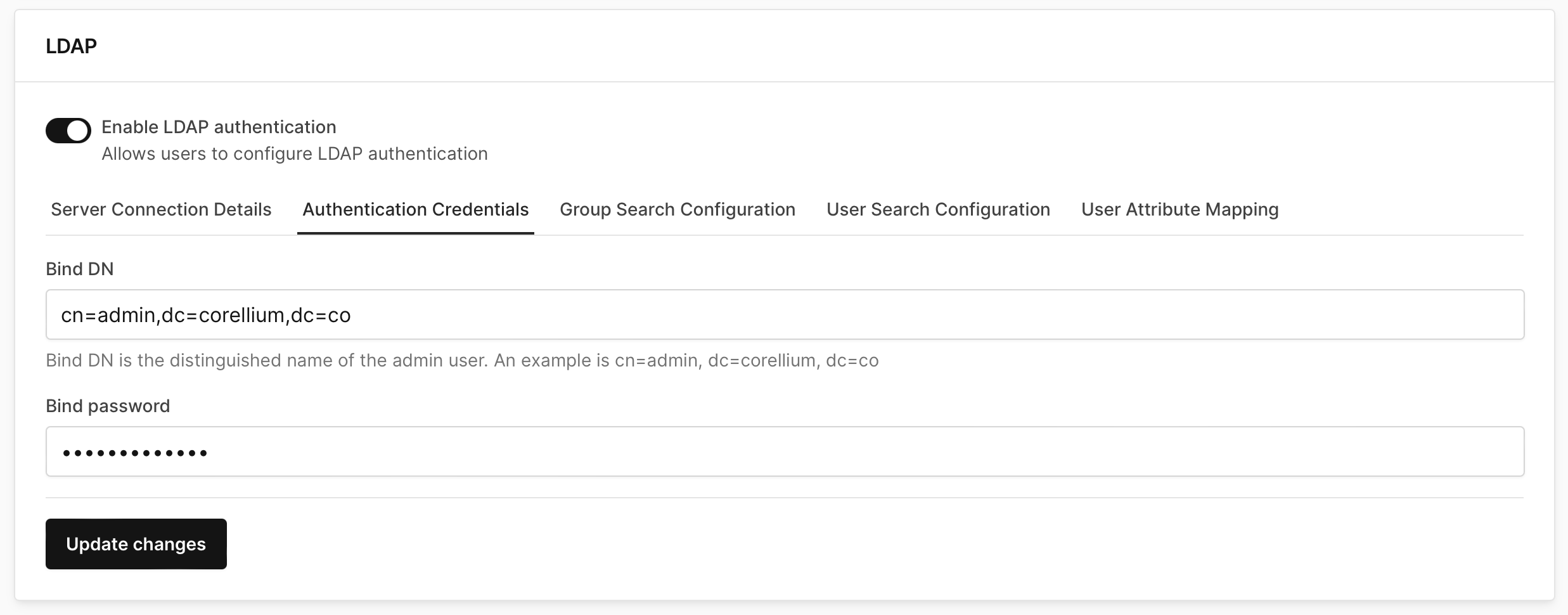
- An example of a Bind DN is
-
Optionally, if you want users to be automatically assigned to Corellium teams, you can configure the Group Search Configuration.
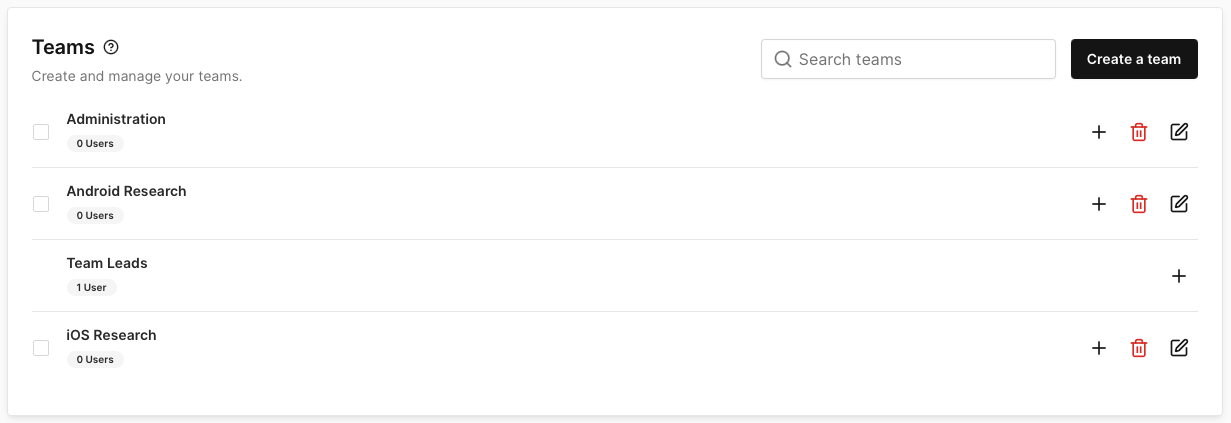
First, create the Corellium teams that will be mapped to the corresponding LDAP groups. In the Corellium web interface, navigate to Admin -> Teams. As an example, we'll create the following Corellium teams:
- Administration
- Android Research
- iOS Research
These are the example LDAP groups we'll be using, with a member included under each group:
# iOS Research Team
dn: cn=ios-research,ou=research,ou=groups,dc=corellium,dc=co
objectClass: groupOfNames
cn: ios-research
description: iOS Platform Research Team
member: cn=alice.dev,ou=users,dc=corellium,dc=co
member: cn=bob.dev,ou=users,dc=corellium,dc=co
# Android Research Team
dn: cn=android-research,ou=research,ou=groups,dc=corellium,dc=co
objectClass: groupOfNames
cn: android-research
description: Android Platform Research Team
member: cn=bob.dev,ou=users,dc=corellium,dc=co
# Administration Team
dn: cn=system-administrators,ou=admin,ou=groups,dc=corellium,dc=co
objectClass: groupOfNames
cn: system-administrators
description: Full System Access
member: cn=alice.dev,ou=users,dc=corellium,dc=co
member: cn=carol.mgr,ou=users,dc=corellium,dc=coWe want each group's members to be mapped to the correct Corellium team so all users under the LDAP group who log into the Corellium domain will be automatically assigned to that team.
- Group DN: The LDAP Group DN that contains the users.
- Roles: Determines user privileges.
- User: Standard user without admin permissions.
- Admin: User with domain administration privileges.
- Team: The Corellium team the members will be automatically added to.
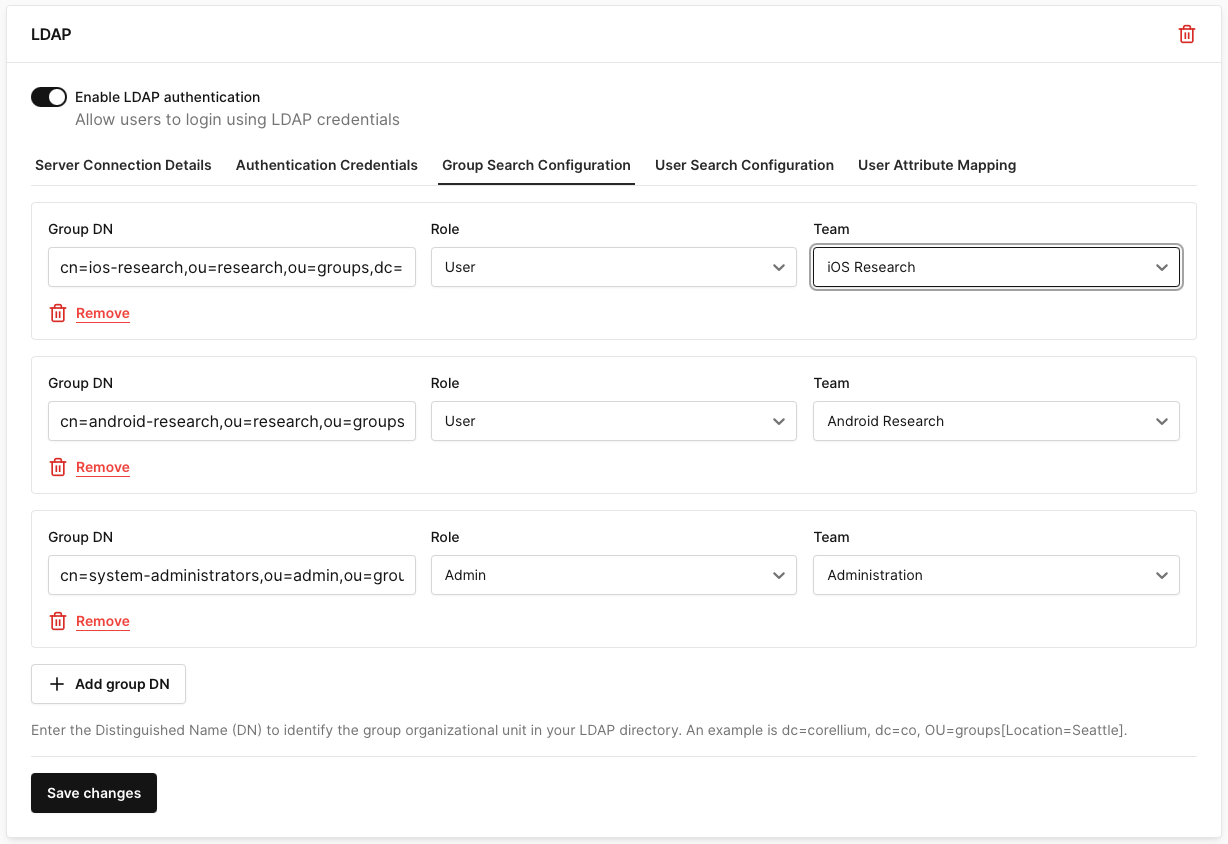
For the iOS Research Team LDAP group, we'll use the following values:
- Group DN:
cn=ios-research,ou=research,ou=groups,dc=corellium,dc=co - Role: Users
- Team: iOS Research
For the Android Research Team LDAP group, we'll use:
- Group DN:
cn=android-research,ou=research,ou=groups,dc=corellium,dc=co - Role: Users
- Team: Android Research
For the Administration Team, we want these members apart of this group to have domain administrator permissions:
- Group DN:
cn=system-administrators,ou=admin,ou=groups,dc=corellium,dc=co - Role: Admin
- Team: Administration
Next, we'll create the Corellium projects under Admin -> Projects that we'll assign the Corellium teams to.
For each project you want to assign a team to, click on the project when under the Projects tab and under the Permissions section, click "Assign a user or team".
- Project permissions:
- Member: Users will be able to see and create devices inside this project.
- Admin: Different than domain administration privileges, users will be able to configure the project settings only for the assigned project.
We want members of the iOS Researcher team assigned as members of the iOS Research Project.
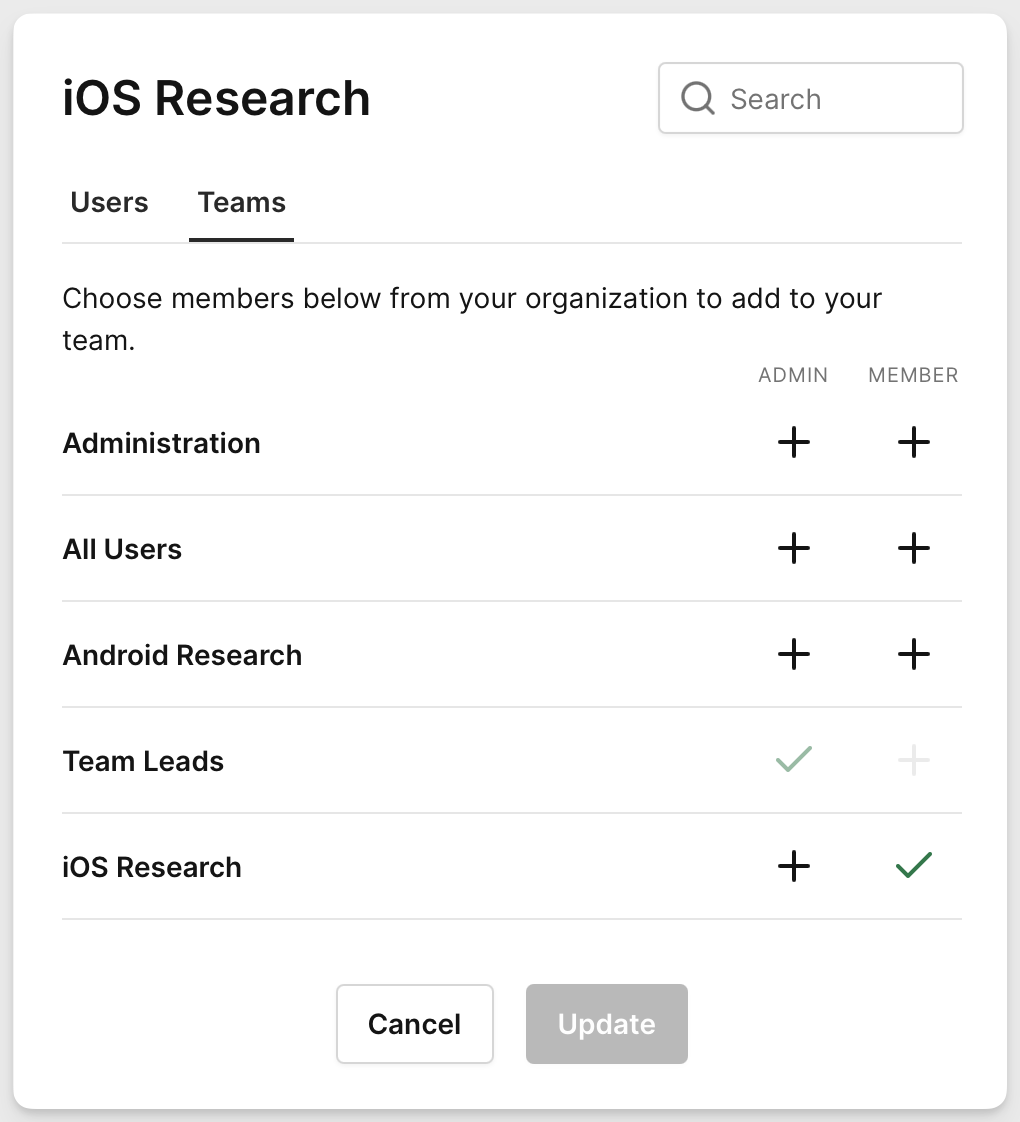
Members of the Android Researcher team we want assigned as members of the Android Research Project.
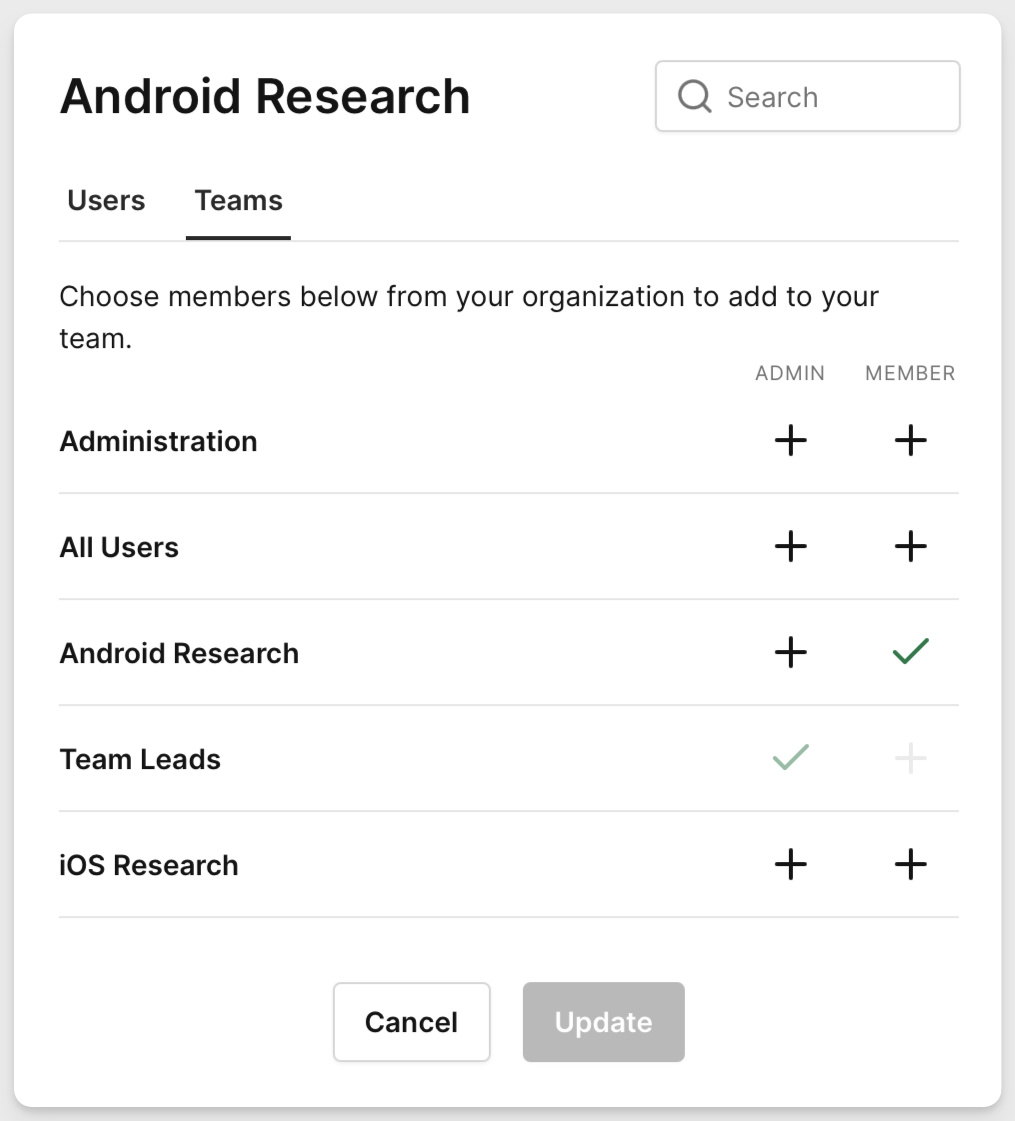
For members of the Administration Corellium team, because we assigned the role "Admin" we don't need to assign this team to a Corellium project. These users will have full control over the domain and be able to view and configure any projects a part of the domain.
-
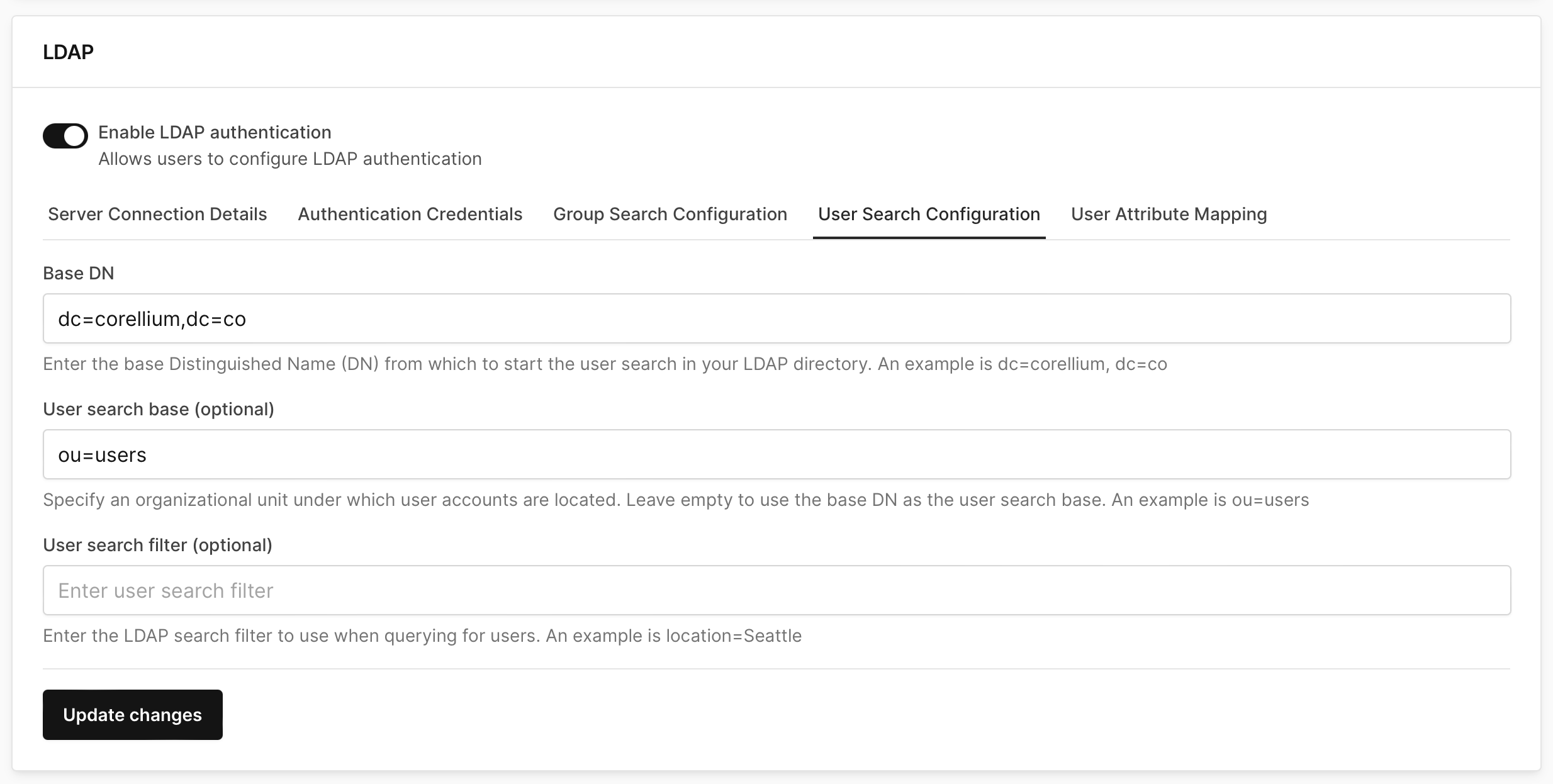
In the User Search Configuration tab, set the Base Distinguished Name for your organization from which to start the user search in your LDAP directory. We'll be using
dc=corellium,dc=coas an example.If you choose to not set the organization unit (OU) in Base DN, set the OU in the User Search Base field.
- You can also specify a User Search Filter for querying users, such as by location.
-
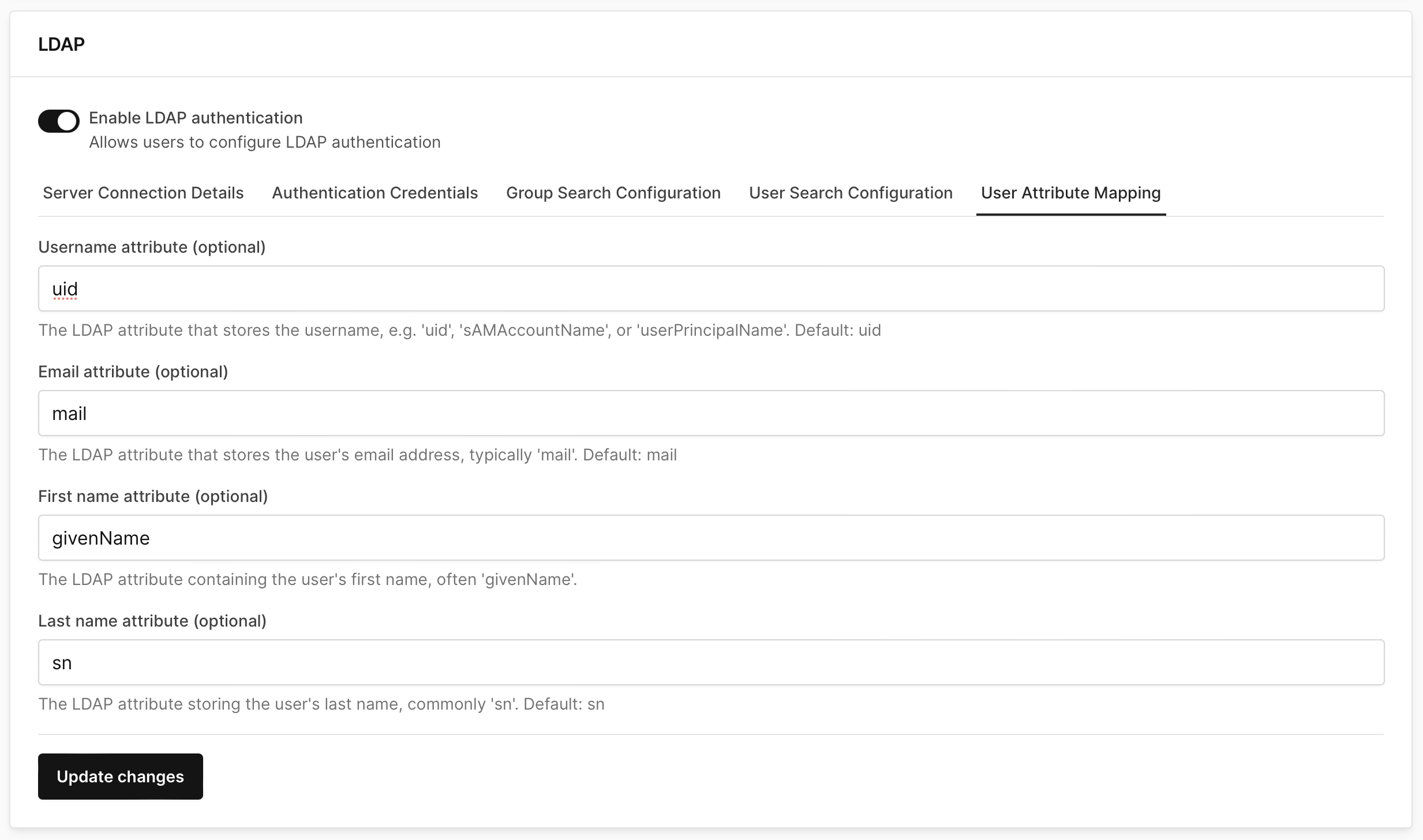
In the User Attribute Mapping tab, specify the username, email, first name, and last name mapping for the LDAP users.
infoThe username value is used for logging into the domain. Be sure to specify the correct LDAP attribute that stores this value.
Here's an example of a user LDAP attribute structure:
dn: cn=bob.dev,ou=users,dc=corellium,dc=co
objectClass: inetOrgPerson
cn: bob.dev
sn: Builder
givenName: Bob
uid: bob.dev
mail: [email protected]
title: Research Engineer
description: iOS and Android ResearcherIn our example user attribute LDAP structure, we already send in the username as the
uidLDAP user attribute, so we can leave these fields blank and Bob can log in successfully. This is because Corellium defaults to useuidif nothing is specified.If your user LDAP attributes differ in your implementation of LDAP, please enter the attributes in the web interface that map to the correct values that Corellium uses. A suggestion would be to match your implementation of LDAP's user attribute structure to be what Corellium defaults to.
Log in with LDAP
From the domain login page, click on the new button Sign in with your organization to proceed with LDAP login.
Once authenticated, you will be directed to the Corellium device page.
For our example LDAP setup, we'll log in with the Alice user and the Bob user.
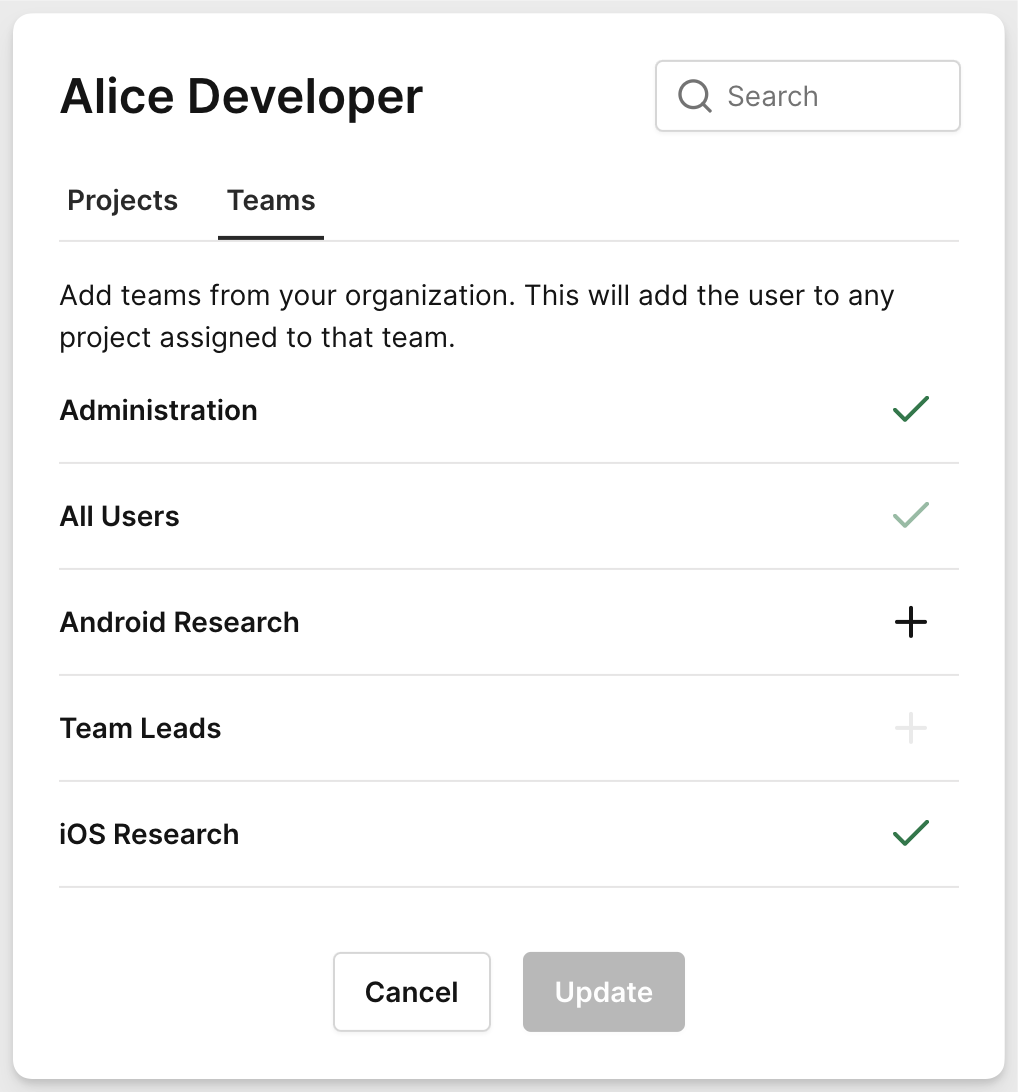
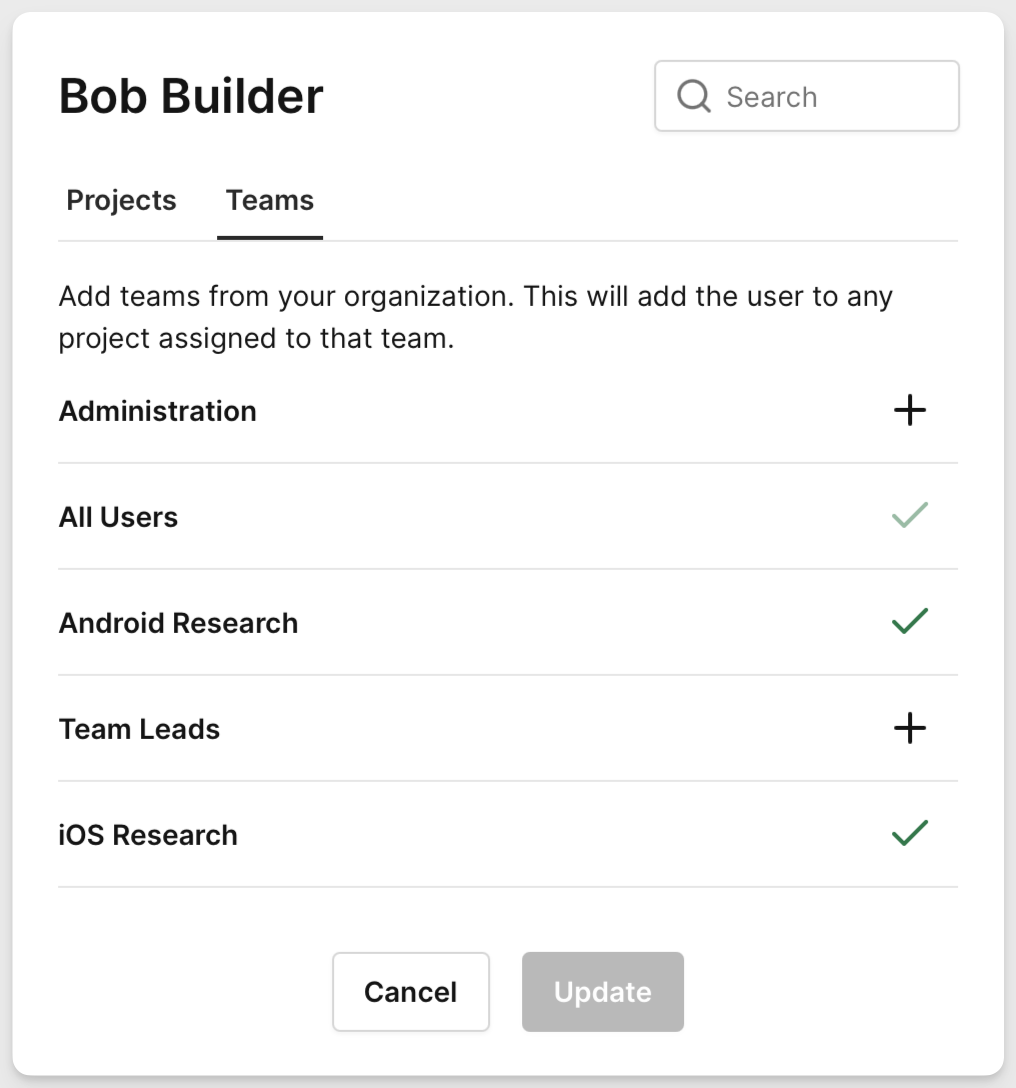
Based on our LDAP configurations in the Corellium web interface, Alice will automatically be assigned to the iOS Research team and granted domain administrator privileges. Meanwhile, Bob will have standard user privileges and will only be able to view and create devices in Corellium projects where his assigned team has been added.
After logging in, Alice user looks like:
After logging in, Bob user looks like:
Limitations
While LDAP provides a convenient way to manage user authentication, there are a few limitations to be aware of:
-
A user can be a member of a maximum of 50 groups.
-
LDAP in Corellium does not support nested groups.
Example of a nested group:
dn: cn=engineering-team,ou=engineering,ou=groups,dc=corellium,dc=co
objectClass: groupOfNames
cn: engineering-team
description: All iOS and Android Engineers at Corellium
member: cn=ios-research,ou=research,ou=groups,dc=corellium,dc=co
member: cn=android-research,ou=research,ou=groups,dc=corellium,dc=co
Troubleshooting
Please review this section if you encounter any issues with LDAP authentication in Corellium.
For further assistance or specific queries, please refer to our technical support team.
ECONNREFUSED Error
If you encounter an ECONNREFUSED error when trying to connect to your LDAP server, the connection to the LDAP server was refused. This could be due to a misconfiguration in the LDAP server settings or a firewall blocking the connection.
User does not exist Error
A User does not exist error when trying to authenticate with LDAP is likely due to either:
-
The specified user does not exist in the LDAP directory. Please ensure that the LDAP username attribute being used correctly maps to the LDAP user attribute that stores the username in your LDAP implementation.
-
The Base Distinguished Name (DN) might be incorrectly configured. The Base DN is the starting point for the LDAP search and should be correctly set to match your LDAP directory structure. Please verify that it's properly configured.
LDAP Group Search Error
Seeing Login failed! LDAP group search error: null upon login likely means have a blank entry under the Group Search Configuration tab in the web interface. Please ensure all entries are filled out or removed if it's not needed. After making the changes and clicking Save Changes users should be able to log in successfully.
TeamID Error
A team with teamId=8d93fa3a-de94-4c61-8cce-51134edad35e not found error can be seen if the Corellium team being used in the Group Search Configuration is removed after changes have been already saved. You can resolve this by clearing the offending entries from the Group Search Configuration page in the web interface.