Network Monitor
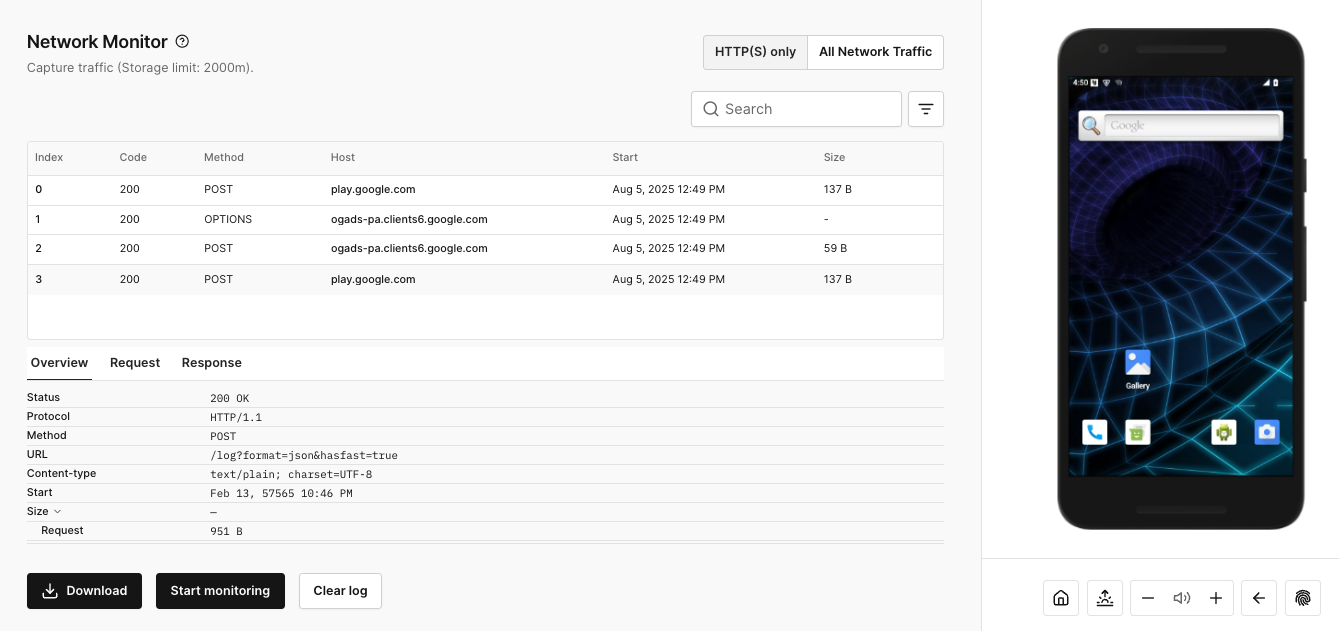
The Network Monitor captures, presents, and monitors HTTPS network traffic, transparently defeating certificate pinning.
To run the Network Monitor, the jailbroken or rooted device must have both Wi-Fi and cellular connectivity enabled.
Capture Network Traffic
Capture all network traffic for native files, as well as applications, in a single click. Captured HTTP and HTTPS network traffic and monitored iOS network traffic will appear in the Overview panel. Open a captured packet to display more information, including an overview, the request, and the response.
Inspect Network Requests
The details panel contains three tabs:
- The Overview tab contains general information on the request.
- The Request tab contains HTTP headers captured when the request was made, as well as the body of requests like POST
- The Response tab contains the same information but for the response to the request.
How It Works
When Network Monitor is active, all VM network traffic is redirected through sslsplit which runs on the same Corellium compute node as the VM. Unencrypted HTTPS network traffic does not leave the node.
Corellium injects a Certificate Authority certificate into the trusted system certificate store.
To defeat certificate pinning, Corellium patches sslsplit, the system's boringssl library, and the integrated WebView's boringssl library. sslsplit is patched to include the original certificate chain inside the generated certificate chain as an X.509 extension. boringssl is patched so that, if the leaf certificate of the original chain includes the X.509 extension, and if the leaf certificate validates against the injected Corellium certificate authority certificate, the original certificate chain is reported to clients of the library rather than the generated certificate chain. This chain is still subject to normal Android and/or boringssl verification rules.