Frida
If you're interested in using Frida, great news, it's already integrated into the UI!
Wait so, what is Frida?
Frida is a dynamic code instrumentation toolkit for developing, researching, and reversing applications. For ease of use, we’ve included a Frida daemon in all jailbroken iOS and rooted Android VMs.
Frida integration only exists on rooted Android and jailbroken iOS devices.
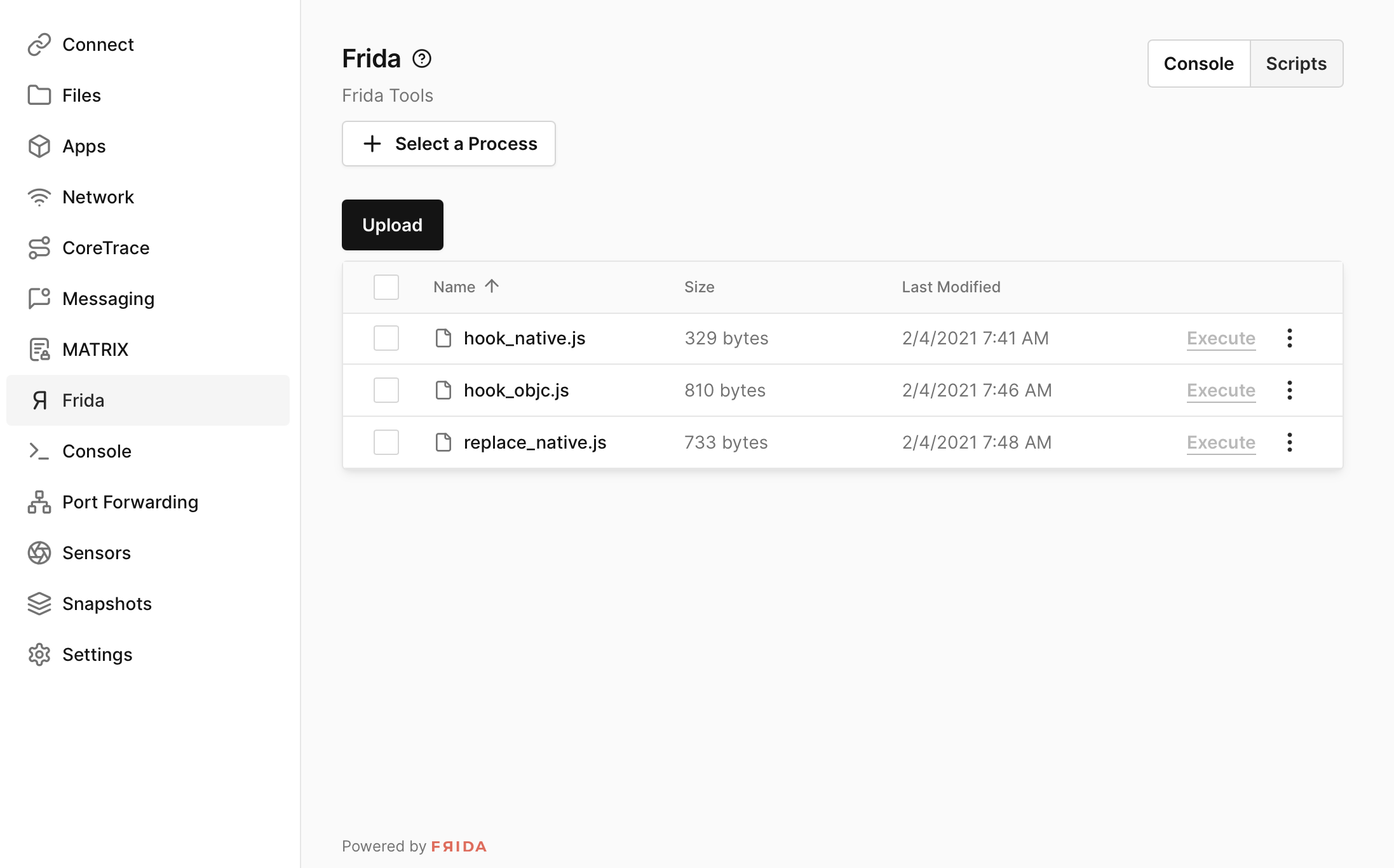
To work with the included frida-server, open the Frida tab (as shown above) and select a process to begin. From there, you can upload, edit, download, and run scripts, attach to processes, and interact with a full Frida console.
You are not able to spawn applications with Frida though the integrated Frida tab, you must use a local frida client or use the device console.
The process list shown by Frida in the web interface is explicitly filtered to exclude any processes that would render an error (such as processes that are statically linked or do not include libc).
Connect Directly with the Built-in frida-server
Rooted Androids and jailbroken iOS devices will include both a built-in frida-server and a Frida client by default.
To start interacting directly with the frida-server from your local machine, you must first connect to the VPN provided on the Connect tab (for cloud users). Check out the connecting to the Corellium VPN article for instructions on how to connect to the VPN. Then, you must connect to the device.
For example, on Android, you must connect to adb. Once the device is connected and the local machine can see it, Frida will forward the necessary ports and connect using adb, which you can test using the frida-ps -U command:
$ frida-ps -U
PID Name
---- -------------------------------------------------------------
396 adbd
1433 android.ext.services
240 [email protected]
315 android.hardware.audio.service
316 [email protected]
419 [email protected]
420 [email protected]
317 [email protected]
...
For iOS, to use the -U argument, make sure you have USBFlux running.
If you want to connect without USBFlux using -H or --host, portforward 27042 for both the Device port and Router Port to the Port Forwarding tab of your device and then use:
frida-ps -H [VM IP ADDRESS]:27042
A common issue when using a local Frida client to interact with the device's built-in frida-server is a version mismatch, see the Identify the Built-in Frida Version guide for more details.
One command which is explicitly different from the stock Frida CLI is the %load command. If you push a file to the device, such as /data/local/tmp, and want to load it into the console, you should use this command.
[Remote::PID::320]-> %load /data/local/tmp/hook_java.js
[+] Hook android.webkit.WebView.loadUrl()...
[Remote::PID::320]->
For further step by step guidance, see Using a Local Frida Client.
Use Frida Entirely from the Virtual Device Console
You can use the built-in Frida client to interact directly with the built-in server through the virtual device's console, this is useful if you need to spawn the application with Frida. You can accomplish this by running your frida command specifying 127.0.0.1:27042.
Here's an example command for iOS to spawn and attach to the Calculator app run directly on the device:
script -q /dev/null frida -H 127.0.0.1:27042 -f com.apple.calculator
The script -q /dev/null is necessary here for iOS to give Frida a pseudo-TTY so prompt_toolkit can run without crashing due to the shell environment on the device not having a valid stdin file descriptor.
Example command for Android to spawn the Files app, it is not guaranteed all apps can be spawned and attached to in this way:
frida --host=127.0.0.1:27042 -f com.android.documentsui
Use Publicly Available Frida Scripts
Frida Codeshare is a public repository of scripts that you can use to interact with applications.
You can use these scripts to do things like bypass SSL pinning, find hooks, defeat root/jailbreak detection, and more. While these scripts are not guaranteed to work, they can serve as useful starting points for your own instrumentation efforts.
Use Objection through Frida
Objection is a powerful open-source runtime mobile exploration toolkit that runs on top of Frida.
Get started using our guide.