VPN
Why Use the VPN?
Using a VPN will put your Virtual Device and the computer you are accessing Corellium from (typically a desktop or laptop computer) on the same network. Common use cases for this are:
- SSH access to the device.
- Access your application via various TCP/IP or UDP ports and protocols from your desktop/laptop computer.
- Kernel debugging.
- Run a
vmmioperipheral over TCP/IP on your local computer to feed stimuli data through a peripheral running locally on your computer into the Virtual Device for application and algorithm validation.
Local Network and Firewall Configuration
This section applies to enterprise-grade networks with restrictive firewalls.
When you connect to the Corellium VPN, you are establishing an outbound UDP connection to AWS servers in the us-east-2 region. AWS assigns the public-facing IP address dynamically, and Corellium does not know which IP addresses AWS will use.
The connection uses ports that are ephemerally created on non-privileged ports (1024 and greater).
Local Firewall Configuration Changes
Some enterprise-grade networks block these connections by default. If this is the case, your network administrator will need to allow access to your firewall by performing the following steps:
- Set up a static outgoing source IP.
- Enable outgoing UDP traffic on all non-privileged ports (1024 and greater) from the static source to all AWS "us-east-2" IP address ranges.
Gather the List of AWS "us-east-2" IP Addresses
-
Please refer to AWS's page discussing IP address ranges.
-
To display the list of IP ranges, download ip-ranges.json and filter only IPv4 for the us-east-2 region.
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r '.prefixes[] | select(.region == "us-east-2") | .ip_prefix'
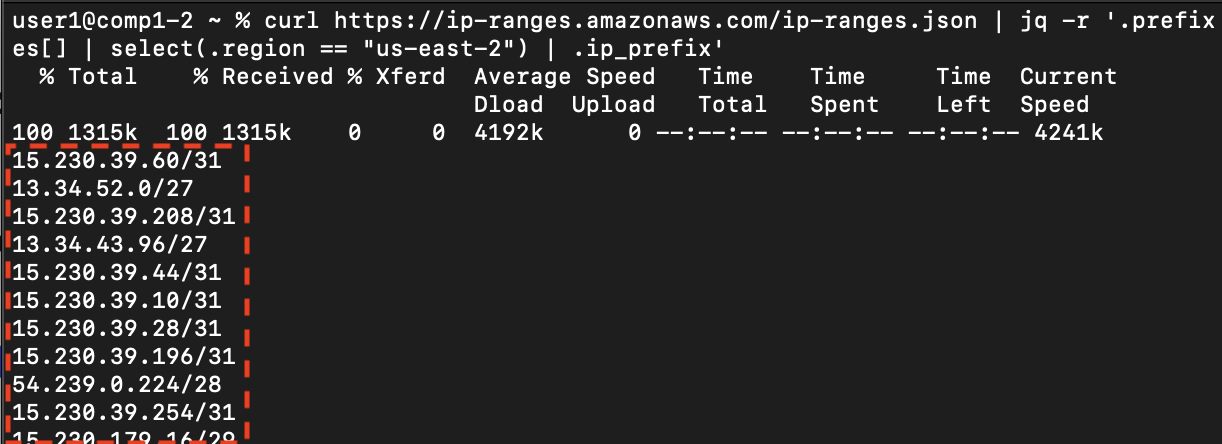
- To save the list, redirect the output to a file.
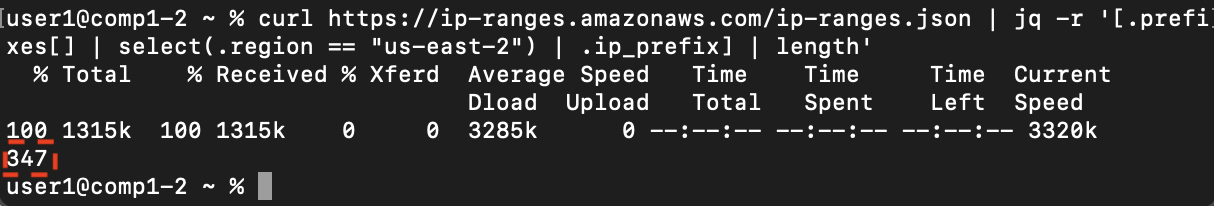
- To see how many IP ranges are included, wrap the
jqcommand in square brackets then find the length of the array. We can see there are 347 sets of IP ranges.
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r '[.prefixes[] | select(.region == "us-east-2") | .ip_prefix] | length'
You should only need to allow connections over IPv4 on us-east-2.
To list IPv4 and IPv6 addresses, run the following:
curl https://ip-ranges.amazonaws.com/ip-ranges.json | jq -r 'to_entries[] | select(.key|contains("prefixes")).value | .[] | select(.region="us-east-2") | to_entries[] | select(.key|contains("prefix")).value'
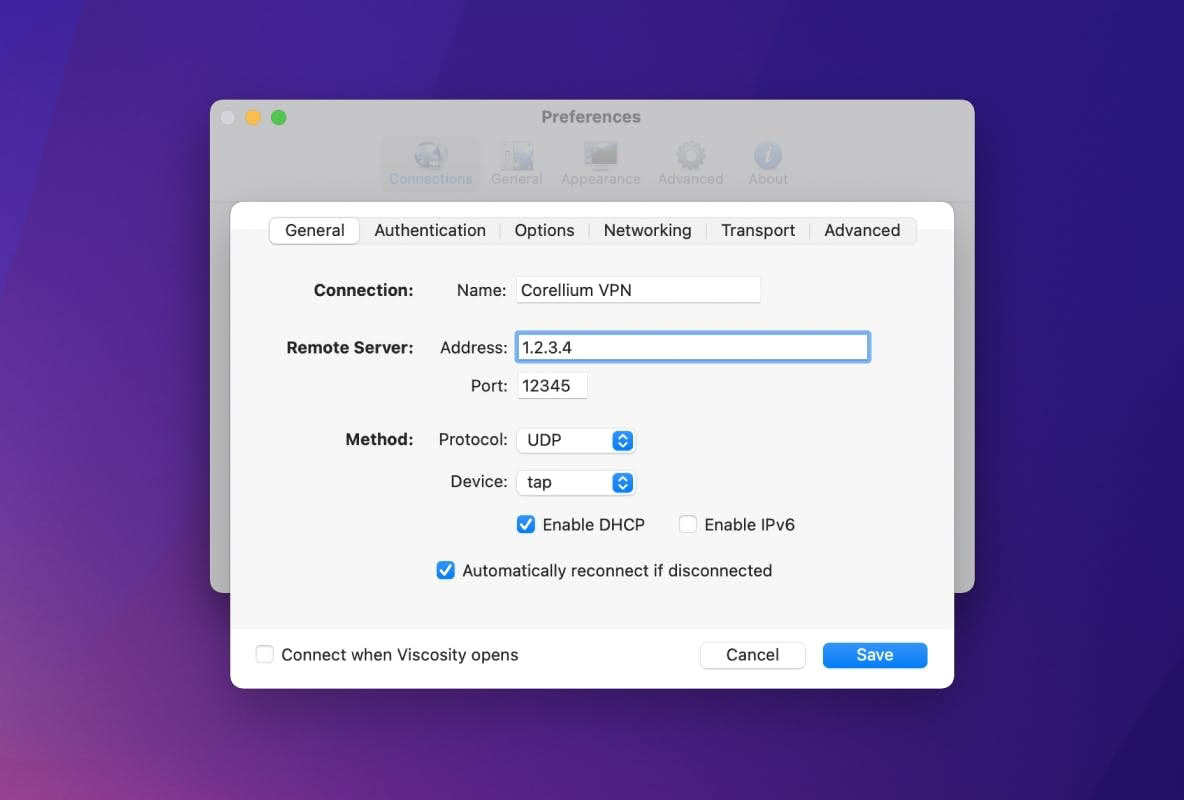
How to Connect with macOS
You will need to use a VPN client that supports TAP mode.
We are aware of two clients that work on macOS:
- Viscosity (recommended)
- TunnelBlick (free)
Follow these steps using either macOS client:
- Install either TunnelBlick or Viscosity OpenVPN client.
- Power on a Corellium virtual device.
- Click Connect and then DOWNLOAD OVPN FILE. Save the file to your local system.

- Import the
.ovpnconfiguration file that you downloaded into your VPN client.
- Connect to the VPN.
How to Connect with Windows OS
Installing OpenVPN on Windows OS
-
Install the appropriate version of OpenVPN for your machine from this URL.
-
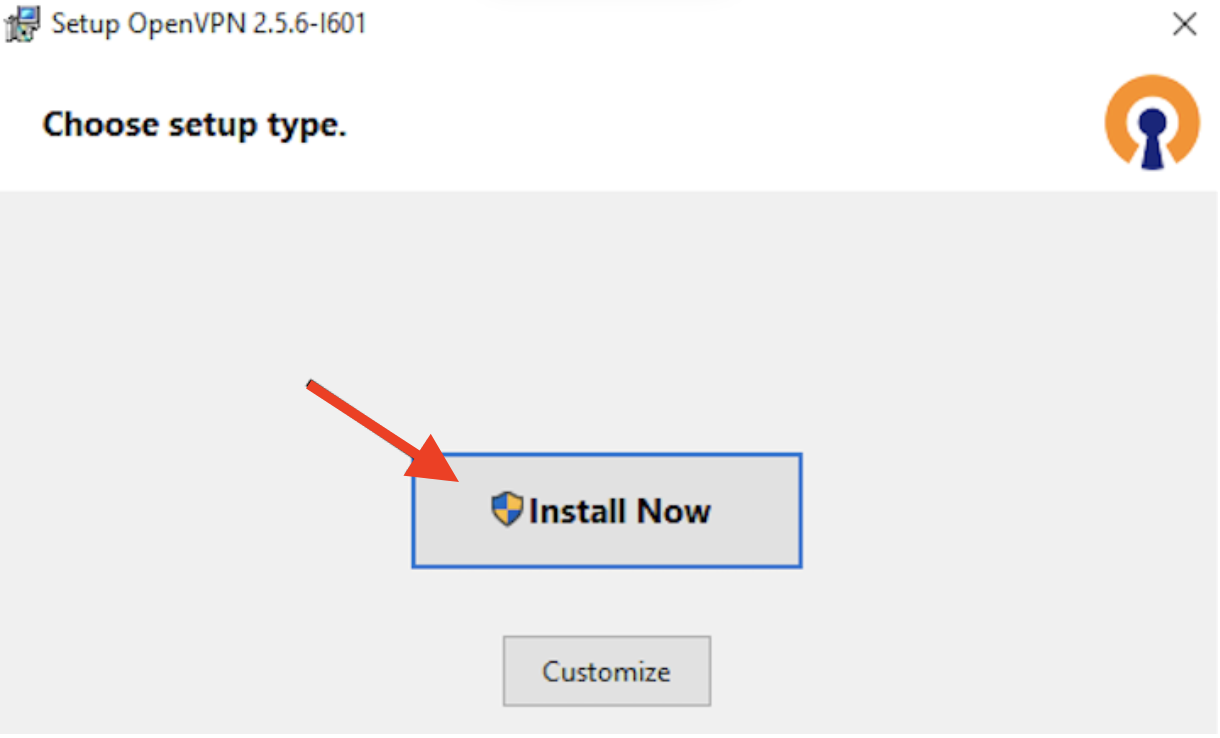
Double-click the downloaded file, then click Install Now.
- The OpenVPN GUI icon should appear in the taskbar by the clock.
Connecting via OpenVPN
- First, click on your device.

- Click CONNECT and then DOWNLOAD OVPN FILE.

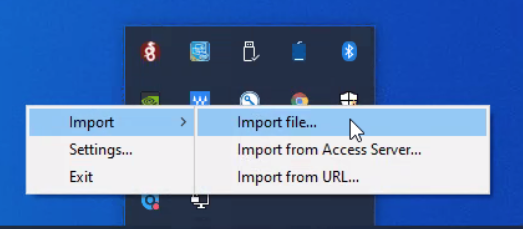
- Right-click on the OpenVPN GUI icon in the taskbar and select Import → Import File.
- Then, select the downloaded OVPN file.
- Right-click on the OpenVPN GUI icon in the taskbar and click Connect.
- This window will appear, and it will close when OpenVPN has connected to the device.
How to Connect with Linux
Use the default OpenVPN package installed by default with Ubuntu 22 LTS.
Connecting via OpenVPN
- First, click on your device.

- Click CONNECT and then DOWNLOAD OVPN FILE.

- Connect to your device using the
.ovpnfile. Note: this command will likely fail withoutsudo.
sudo openvpn --config ~/Downloads/corellium.com\ VPN\ -\ Default\ Project.ovpn
- You should see the following lines in the console response confirming the VPN is set up.
TUN/TAP device tap0 opened
...
net_iface_up: set tap0 up
...
Initialization Sequence Completed
Checking Your Connection
Open a terminal window and SSH into your device, check out our Connect to a Virtual Device via SSH article for instructions.
Important Notes and Troubleshooting Tips
- Make sure you're connecting to the right profile for your project, and that at least one device in your project is in the ON state. If you see an error stating
read UPD [ECONNREFUSED]: Connection refused (code=111)you need to turn on a virtual device. VPN connections are not possible if all project devices are turned off or if the project contains no devices in the project. - If you're having trouble connecting, try re-installing your VPN Profile.
- Close any other VPNs.
- Check that your network doesn't have a firewall preventing your connection. Learn more about configuring Windows Defender Firewall.
- Running other VPNs may interfere with your Corellium VPN connection. If you are having trouble connecting to the Corellium VPN and are already running your own VPN, you may need to disable the other VPN and then reconnect to the Corellium VPN.
- The VPN software must support TAP mode.
- If you are on an Individual Account, you only need to establish one VPN connection to your account, and that connection will work for all devices.
- Intermittent disconnetion issues are likely related to your latency or network firewall. Corellium uses the AWS U.S. East region, so certain geographies will have higher latencies.
- While connected to the VPN, try pinging your device's Services IP twenty times, for example
ping -c20 10.11.1.1. If you see dropped packets or an average ping of more than 100 ms, check your firewall configuration and internet speed.